Hey there, tech enthusiasts! If you're reading this, chances are you're diving headfirst into the world of secure IoT connections. Let me tell you, securely connect remote IoT P2P SSH Ubuntu isn't just a tech buzzword; it's a necessity in today's interconnected world. Imagine your smart devices talking to each other without any hiccups, all while keeping your data safe from prying eyes. Sounds awesome, right? Well, buckle up because we’re about to take you on a journey through the ins and outs of secure IoT connections using SSH on Ubuntu.
Now, let's break it down for you. The keyword here is "securely connect remote IoT P2p SSH Ubuntu." It’s not just about setting up a connection; it’s about doing it right, ensuring your IoT devices are protected, and maintaining a smooth peer-to-peer communication. Whether you're a seasoned IT pro or just starting out, this guide will help you navigate the complexities of SSH on Ubuntu for your IoT projects.
Before we dive deep, let's set the stage. The Internet of Things (IoT) is booming, and with it comes the need for secure connections. SSH (Secure Shell) is your go-to protocol for secure communication between devices. Pair that with Ubuntu, one of the most reliable Linux distributions out there, and you’ve got yourself a powerful setup. So, without further ado, let’s get started!
Read also:Megan Is Missing Is It Real Footage The Truth Behind The Viral Sensation
Understanding SSH and Its Role in IoT
First things first, what exactly is SSH? Simply put, SSH is a cryptographic network protocol that allows you to securely connect to remote devices. Think of it as a secure tunnel that protects your data from hackers and snoopers. When it comes to IoT, SSH plays a crucial role in ensuring that your devices can communicate with each other without any security breaches.
In the context of IoT, SSH provides a secure channel for data transfer, command execution, and file management. It’s like having a private line of communication between your devices, ensuring that no one else can eavesdrop or tamper with your data. And with Ubuntu, you get a robust platform that supports SSH out of the box, making it an ideal choice for your IoT projects.
Why Choose SSH for IoT Devices?
- Security: SSH encrypts all communication, making it nearly impossible for attackers to intercept your data.
- Reliability: SSH ensures that your connections remain stable, even in less-than-ideal network conditions.
- Flexibility: With SSH, you can manage multiple devices from a single point, streamlining your IoT operations.
Setting Up SSH on Ubuntu for IoT
Alright, let’s get our hands dirty. Setting up SSH on Ubuntu is relatively straightforward, but there are a few steps you need to follow to ensure everything runs smoothly. First, make sure your Ubuntu system is up to date. You don’t want to start with outdated software, do you?
Once your system is updated, install the SSH server. This can be done using the terminal with a simple command. Don’t worry if you’re not a terminal wizard; we’ll guide you through it. After installation, configure your SSH settings to suit your IoT needs. This includes setting up firewalls, managing user permissions, and configuring SSH keys for added security.
Step-by-Step Guide to Installing SSH on Ubuntu
- Update your system:
sudo apt update && sudo apt upgrade. - Install SSH server:
sudo apt install openssh-server. - Start the SSH service:
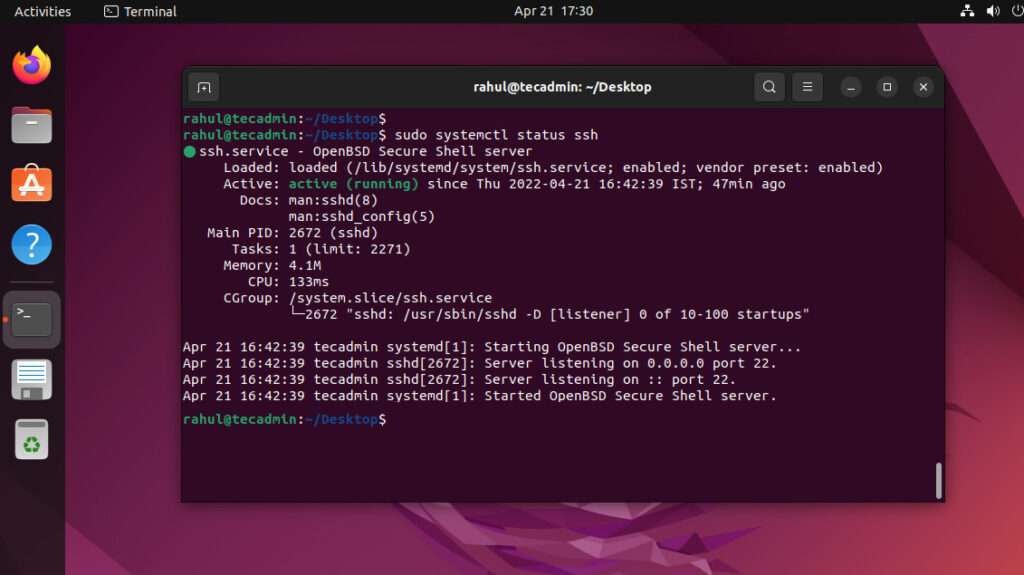
sudo systemctl start ssh. - Check the status:
sudo systemctl status ssh.
Configuring SSH for Secure IoT Connections
Now that you’ve got SSH up and running, it’s time to configure it for your IoT devices. This involves tweaking your SSH settings to ensure maximum security. One of the most important steps is setting up SSH keys. These keys act as a digital ID card, allowing only authorized devices to connect to your network.
Another crucial step is configuring your firewall. This helps prevent unauthorized access to your IoT devices. You can use tools like UFW (Uncomplicated Firewall) to manage your firewall settings easily. Additionally, consider disabling password authentication and only allowing key-based authentication for added security.
Read also:Sone 436 Japanese Your Ultimate Guide To Discovering This Cultural Gem
Best Practices for SSH Configuration
- Use SSH Keys: Generate and use SSH keys for authentication instead of passwords.
- Disable Root Login: Restrict root access to prevent unauthorized users from gaining admin privileges.
- Limit User Access: Only allow specific users to access your IoT devices via SSH.
Peer-to-Peer Communication with SSH
One of the coolest things about SSH is its ability to facilitate peer-to-peer (P2P) communication between devices. This is particularly useful in IoT setups where devices need to communicate directly without relying on a central server. By setting up SSH tunnels, you can create secure P2P connections that allow your devices to share data seamlessly.
To achieve this, you’ll need to configure your SSH settings to allow tunneling. This involves setting up port forwarding rules and ensuring that your devices can communicate with each other over the SSH protocol. With the right configuration, your IoT devices can form a secure P2P network, enhancing their functionality and efficiency.
Setting Up SSH Tunnels for P2P Communication
- Enable Port Forwarding: Configure your SSH server to allow port forwarding.
- Set Up SSH Tunnels: Use the SSH command to establish tunnels between your devices.
- Test the Connection: Ensure that your devices can communicate with each other over the SSH tunnel.
Managing Remote IoT Devices with SSH
Once your SSH setup is complete, it’s time to start managing your IoT devices remotely. With SSH, you can execute commands, transfer files, and monitor your devices from anywhere in the world. This is particularly useful if you have IoT devices deployed in remote locations.
Tools like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol) make it easy to transfer files between your devices. Additionally, you can use SSH to monitor the status of your devices, check logs, and troubleshoot issues in real-time. This level of control ensures that your IoT network remains healthy and functional at all times.
Tools for Remote IoT Management
- SCP: Use SCP to securely transfer files between your devices.
- SFTP: Use SFTP for more advanced file management tasks.
- SSH Commands: Execute remote commands to manage your IoT devices.
Securing Your IoT Network
Security is paramount when it comes to IoT. Even with SSH in place, there are additional steps you can take to secure your IoT network. This includes regular updates, monitoring for suspicious activity, and implementing intrusion detection systems (IDS).
Regularly updating your software and firmware ensures that any security vulnerabilities are patched. Monitoring your network for unusual activity can help you detect and respond to potential threats quickly. And with an IDS in place, you can automatically detect and respond to intrusions, keeping your IoT network safe and secure.
Advanced Security Measures
- Regular Updates: Keep your software and firmware up to date.
- Network Monitoring: Use tools to monitor your network for suspicious activity.
- Intrusion Detection: Implement an IDS to automatically detect and respond to threats.
Troubleshooting Common SSH Issues
No matter how well you set things up, issues can arise. Whether it’s a connection problem or a configuration error, knowing how to troubleshoot SSH issues is essential. Common problems include incorrect SSH keys, firewall blocks, and misconfigured settings.
To troubleshoot these issues, start by checking your SSH logs for any error messages. Verify that your SSH keys are correctly set up and that your firewall rules allow SSH traffic. If the problem persists, consult the official SSH documentation or seek help from the vibrant Ubuntu community.
Common SSH Troubleshooting Tips
- Check Logs: Review SSH logs for error messages.
- Verify Keys: Ensure that your SSH keys are correctly configured.
- Test Firewall: Confirm that your firewall allows SSH traffic.
Conclusion: Securely Connect Remote IoT P2P SSH Ubuntu
Well, there you have it, folks! Securely connect remote IoT P2P SSH Ubuntu is all about setting up a secure, reliable, and efficient network for your IoT devices. By following the steps outlined in this guide, you can ensure that your devices are protected and functioning optimally.
Remember, security is an ongoing process. Regular updates, monitoring, and implementing advanced security measures are crucial to maintaining a secure IoT network. So, keep learning, keep experimenting, and most importantly, keep your data safe!
And hey, don’t forget to share this article with your fellow tech enthusiasts. The more we spread the knowledge, the better we can protect our IoT networks. Drop a comment below if you have any questions or if there’s anything else you’d like to know. Happy tinkering!
Table of Contents
- Understanding SSH and Its Role in IoT
- Setting Up SSH on Ubuntu for IoT
- Configuring SSH for Secure IoT Connections
- Peer-to-Peer Communication with SSH
- Managing Remote IoT Devices with SSH
- Securing Your IoT Network
- Troubleshooting Common SSH Issues
- Conclusion: Securely Connect Remote IoT P2P SSH Ubuntu