Hey there, tech enthusiasts! Let's dive straight into the heart of modern tech wizardry. If you're reading this, chances are you're already knee-deep in the world of IoT, cloud computing, and secure connections. Today, we're talking about remoteIoT SSH AWS example, and trust me, it's a game-changer for anyone looking to level up their tech skills. Whether you're a seasoned pro or just starting your journey, this guide is packed with insights and practical tips that’ll make your life easier.
So, why the buzz around remoteIoT SSH AWS example? Well, it’s all about bridging the gap between physical devices and cloud infrastructure. Imagine being able to remotely manage and secure your IoT devices with just a few commands. Sounds cool, right? But before we get too far ahead of ourselves, let’s break it down and understand what makes this setup so powerful.
In this article, we’ll explore everything you need to know about integrating IoT devices with AWS using SSH. From setting up secure connections to troubleshooting common issues, we’ve got you covered. So, buckle up and let’s unravel the secrets of remoteIoT SSH AWS example together!
Read also:Ashton Forbes Bio The Ultimate Guide To His Life Career And Achievements
Here’s a quick overview of what we’ll cover:
- What is RemoteIoT SSH AWS Example?
- Why Use AWS for IoT Devices?
- Setting Up Your First SSH Connection
- Best Practices for Secure Connections
- Common Issues and How to Fix Them
- Real-World Examples and Use Cases
What is RemoteIoT SSH AWS Example?
Alright, let’s start with the basics. RemoteIoT SSH AWS example refers to the process of connecting and managing IoT devices remotely using SSH (Secure Shell) protocols within the AWS ecosystem. In simpler terms, it’s like giving your IoT devices a virtual handshake from anywhere in the world, ensuring they stay secure and functional.
SSH is a cryptographic network protocol that provides a secure channel over an unsecured network. When combined with AWS, it becomes a powerhouse for managing large-scale IoT deployments. AWS offers a robust platform with services like AWS IoT Core, AWS Lambda, and Amazon EC2, making it the perfect partner for your IoT adventures.
Now, here’s the kicker: using SSH with AWS ensures that your data remains encrypted and protected from prying eyes. Whether you’re monitoring smart home devices or managing industrial sensors, the combination of remoteIoT SSH AWS example is your golden ticket to seamless operations.
Why SSH is Essential for IoT Devices
Let’s face it—IoT devices are everywhere. From wearables to smart cities, the possibilities are endless. But with great power comes great responsibility, and that’s where SSH comes in. Here are a few reasons why SSH is a must-have for IoT:
- Security: SSH encrypts all communication between devices, making it nearly impossible for hackers to intercept sensitive data.
- Remote Access: With SSH, you can manage your devices from anywhere, anytime, as long as you have an internet connection.
- Automation: Automate routine tasks like software updates and configuration changes without lifting a finger.
- Scalability: SSH can handle multiple devices simultaneously, making it ideal for large-scale deployments.
Why Use AWS for IoT Devices?
When it comes to IoT, AWS is the go-to platform for many developers and businesses. But what makes AWS so special? Let’s break it down:
Read also:Meet Desta Ostapyks Husband The Ultimate Guide To Their Love Story
First off, AWS offers a wide range of services tailored specifically for IoT. AWS IoT Core, for instance, allows you to connect billions of devices and interact with them securely. Plus, AWS integrates seamlessly with other services like Amazon S3 for storage and AWS Lambda for serverless computing.
Another major advantage of AWS is its scalability. As your IoT deployment grows, AWS can easily scale to meet your needs without breaking a sweat. And let’s not forget about the reliability factor. AWS data centers are spread across the globe, ensuring your devices stay connected no matter where they are.
Key Features of AWS for IoT
Here are some of the standout features of AWS for IoT:
- AWS IoT Core: A managed cloud service that lets you connect IoT devices easily and securely.
- AWS Lambda: Run code in response to events without provisioning or managing servers.
- Amazon S3: Store and retrieve data for your IoT applications.
- AWS CloudWatch: Monitor your IoT devices and applications in real-time.
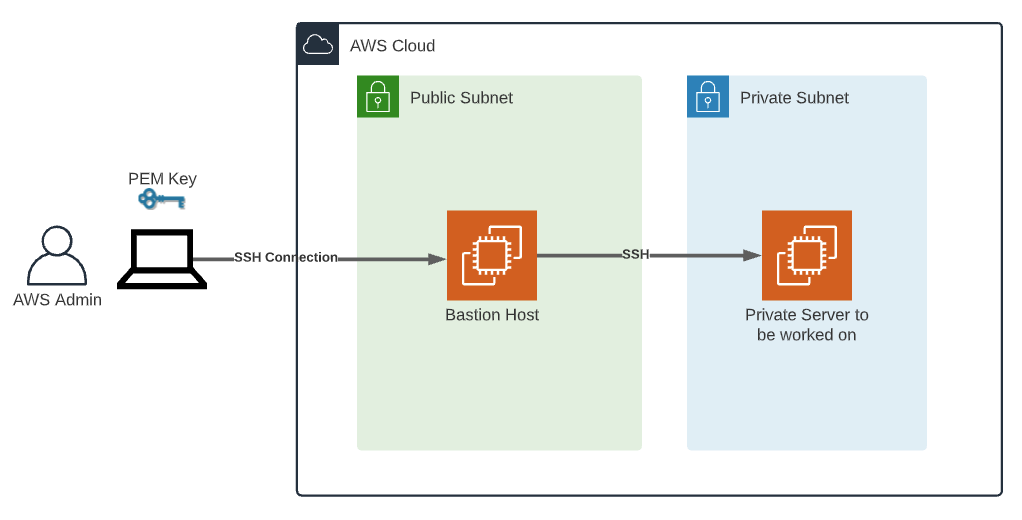
Setting Up Your First SSH Connection
Now that we’ve covered the basics, let’s get our hands dirty and set up your first SSH connection. This step-by-step guide will walk you through the process, ensuring you’re up and running in no time.
Step 1: Install SSH Client
Before you can connect to your IoT device, you’ll need an SSH client. If you’re using Windows, PuTTY is a popular choice. For macOS and Linux users, SSH is already built into the terminal.
Step 2: Generate SSH Keys
Security is key (pun intended), so let’s generate some SSH keys. Open your terminal and run the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This will create a public and private key pair. Keep your private key safe—it’s like the password to your device.
Step 3: Connect to Your Device
With your keys in place, it’s time to connect. Use the following command to establish an SSH connection:
ssh username@your_device_ip
Replace "username" and "your_device_ip" with the appropriate details for your device. If everything goes smoothly, you should now be connected!
Best Practices for Secure Connections
Now that you’re connected, let’s talk about best practices to keep your devices secure. Here are a few tips to follow:
- Use Strong Passwords: Avoid using simple or default passwords. Opt for complex combinations of letters, numbers, and symbols.
- Limit Access: Restrict SSH access to trusted IP addresses to minimize the risk of unauthorized access.
- Enable Two-Factor Authentication: Add an extra layer of security by requiring a second form of verification.
- Regularly Update Software: Keep your devices and software up to date to protect against vulnerabilities.
Common SSH Vulnerabilities
While SSH is incredibly secure, it’s not foolproof. Here are some common vulnerabilities to watch out for:
- Brute Force Attacks: Hackers attempt to guess your password by trying different combinations.
- Man-in-the-Middle Attacks: Attackers intercept communication between your device and the server.
- Configuration Errors: Mishandling SSH settings can leave your devices exposed.
Common Issues and How to Fix Them
Even the best-laid plans can go awry, so let’s tackle some common issues you might encounter:
Issue 1: Connection Timeout
If you’re experiencing connection timeouts, check the following:
- Ensure your device is connected to the internet.
- Verify that the SSH service is running on your device.
- Check your firewall settings to make sure they’re not blocking the connection.
Issue 2: Permission Denied
Getting a "permission denied" error? Here’s what you can do:
- Double-check your SSH keys to ensure they’re correct.
- Make sure the user you’re logging in as has the necessary permissions.
- Verify that the SSH service is configured to allow key-based authentication.
Real-World Examples and Use Cases
Let’s bring it all together with some real-world examples of how remoteIoT SSH AWS example is being used:
Example 1: Smart Agriculture
In the world of agriculture, IoT devices are revolutionizing the way farmers monitor their crops. By connecting sensors to AWS and using SSH for secure communication, farmers can track soil moisture, temperature, and other vital metrics in real-time.
Example 2: Industrial Automation
Manufacturing plants rely heavily on IoT devices to monitor machinery and optimize production. With remoteIoT SSH AWS example, engineers can remotely access and manage these devices, reducing downtime and increasing efficiency.
Example 3: Smart Homes
Smart home devices like thermostats and security cameras are becoming increasingly popular. Using SSH with AWS allows homeowners to securely manage their devices from anywhere, ensuring their homes are always safe and comfortable.
Advanced Techniques for RemoteIoT SSH AWS Example
Once you’ve mastered the basics, it’s time to take your skills to the next level. Here are a few advanced techniques to explore:
Automating Tasks with Scripts
Use bash or Python scripts to automate repetitive tasks like backups and updates. This not only saves time but also reduces the risk of human error.
Monitoring with AWS CloudWatch
Set up alerts and notifications using AWS CloudWatch to stay informed about the status of your devices. This way, you’ll know immediately if something goes wrong.
Scaling with AWS Lambda
As your IoT deployment grows, AWS Lambda can help you scale automatically. Write functions that trigger in response to specific events, ensuring your system stays efficient and responsive.
Conclusion
And there you have it—a comprehensive guide to mastering remoteIoT SSH AWS example. From setting up your first connection to exploring advanced techniques, we’ve covered everything you need to know to take your IoT skills to the next level.
Remember, the key to success lies in staying secure and up to date. Follow best practices, keep an eye on emerging trends, and don’t be afraid to experiment. The world of IoT is vast and ever-evolving, and with tools like AWS and SSH at your disposal, the possibilities are truly endless.
So, what are you waiting for? Dive in, explore, and let us know how it goes. Feel free to leave a comment below or share this article with your fellow tech enthusiasts. Together, let’s build a smarter, more connected world!