Hey there, tech enthusiasts and cloud ninjas! If you're diving into the world of IoT and cloud computing, you're probably wondering how to access IoT SSH AWS securely. Let’s face it—connecting your IoT devices to the cloud can be both exciting and a little overwhelming. But don’t sweat it! In this guide, we’ll break down everything you need to know about securely accessing IoT devices via SSH on AWS. Whether you're a seasoned pro or just starting out, this is the place to be. So grab your favorite drink, sit back, and let’s dive in!
Now, before we get into the nitty-gritty, let’s talk about why this matters. IoT devices are everywhere these days, from smart homes to industrial automation. But with great power comes great responsibility, right? You want to make sure your IoT devices are as secure as Fort Knox. That’s where AWS comes in. By leveraging AWS services, you can create a secure and scalable environment for your IoT devices. And that’s exactly what we’ll be covering here.
So, are you ready to level up your IoT game? Let’s explore how to securely access your IoT devices using SSH on AWS. Buckle up, because this is going to be a wild ride!
Read also:Sone 436 Japanese Your Ultimate Guide To Discovering This Cultural Gem
Understanding the Basics of IoT SSH AWS
First things first, let’s start with the basics. What exactly is IoT SSH AWS? Simply put, it’s the process of accessing your IoT devices remotely using SSH (Secure Shell) through Amazon Web Services. SSH is like a secret handshake that lets you securely connect to your devices over the internet. And AWS? Well, it’s the powerhouse that makes it all possible.
When you’re working with IoT devices, security is key. You don’t want some random hacker getting into your smart fridge or industrial sensor. That’s why using SSH on AWS is such a game-changer. It gives you a secure way to manage and monitor your devices from anywhere in the world. Plus, AWS offers a ton of tools and services to help you keep your data safe.
Why Use AWS for IoT SSH?
There are plenty of reasons why AWS is the go-to platform for IoT SSH. First off, it’s super scalable. Whether you have a handful of devices or thousands, AWS can handle it all. Plus, it integrates seamlessly with other AWS services like AWS IoT Core, Lambda, and S3. This means you can build complex workflows and automate tasks without breaking a sweat.
Another big advantage is security. AWS has built-in security features like IAM roles, VPCs, and encryption that make it tough for bad actors to get in. And let’s not forget about compliance. AWS is compliant with a ton of industry standards, so you can rest easy knowing your data is protected.
Setting Up Your IoT Devices for SSH Access
Alright, now that you know why AWS is the best choice for IoT SSH, let’s talk about how to set it up. The first step is to prepare your IoT devices for remote access. This involves configuring your devices to accept SSH connections and setting up the necessary security measures.
Configuring IoT Devices for SSH
Here’s a quick rundown of what you need to do:
Read also:Unleashing The Power Of Vega Movies Website Your Ultimate Movie Hub
- Install an SSH server on your IoT device. Most Linux-based devices come with OpenSSH pre-installed, but you may need to enable it.
- Generate SSH keys for secure authentication. This is way better than using passwords, trust me.
- Set up a static IP address or use a dynamic DNS service to make it easier to connect to your device.
- Make sure your device’s firewall allows incoming SSH connections.
Once you’ve done all that, your device should be ready to accept SSH connections. But wait, there’s more! Before you start connecting, you’ll need to set up a secure environment on AWS.
Creating a Secure Environment on AWS
Now that your IoT devices are ready, it’s time to set up a secure environment on AWS. This involves creating a VPC (Virtual Private Cloud), setting up security groups, and configuring IAM roles.
Setting Up a VPC
A VPC is like a virtual data center in the cloud. It allows you to create a private network where you can launch your AWS resources. Here’s how to set it up:
- Create a new VPC in the AWS Management Console.
- Set up subnets for your IoT devices and any other resources you want to include.
- Configure route tables and internet gateways to control how traffic flows in and out of your VPC.
By setting up a VPC, you can isolate your IoT devices from the rest of the internet, making them much harder to hack.
Configuring Security Groups
Security groups act like virtual firewalls for your AWS resources. They control which traffic is allowed to reach your devices. Here’s how to configure them:
- Create a new security group in the AWS Management Console.
- Add rules to allow incoming SSH connections on port 22.
- Restrict access to specific IP addresses or ranges to further enhance security.
With security groups in place, you can rest assured that only authorized users can access your IoT devices.
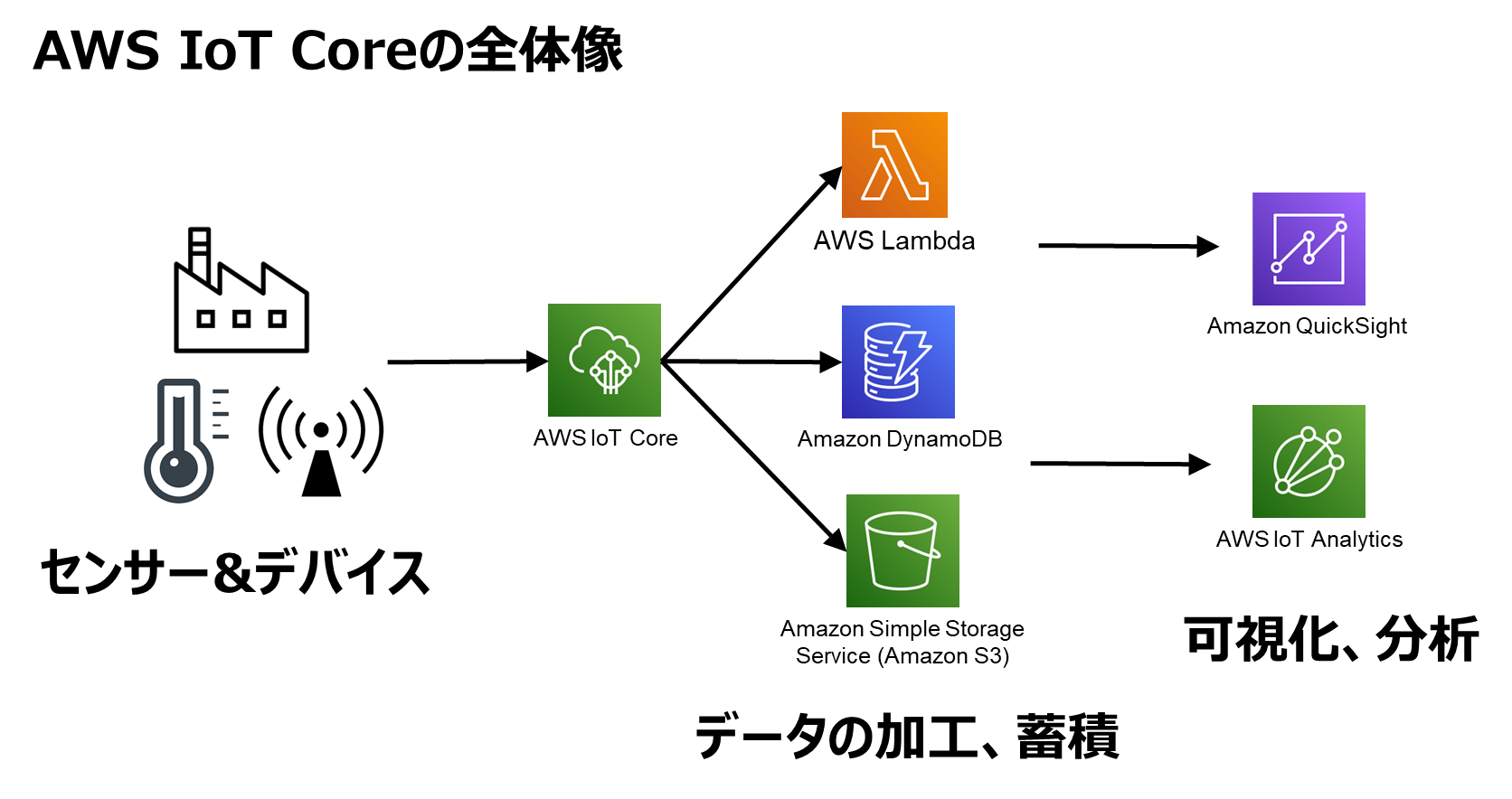
Using AWS IoT Core for Device Management
Now that your devices are securely connected to AWS, it’s time to start managing them. AWS IoT Core is a fully managed service that makes it easy to connect, monitor, and manage your IoT devices at scale.
Connecting Devices to AWS IoT Core
Here’s how to connect your devices to AWS IoT Core:
- Create a thing in AWS IoT Core for each of your devices.
- Generate certificates and policies to authenticate your devices.
- Install the AWS IoT Device SDK on your devices to enable communication with AWS IoT Core.
Once your devices are connected, you can start sending and receiving messages using MQTT or HTTP protocols.
Monitoring Device Activity
AWS IoT Core also lets you monitor your devices in real-time. You can track things like connection status, message traffic, and device health. This is super useful for troubleshooting and ensuring your devices are running smoothly.
Implementing Best Practices for IoT SSH AWS
Now that you know how to set up and manage your IoT devices on AWS, let’s talk about best practices. These tips will help you keep your devices secure and running smoothly.
Using SSH Keys Instead of Passwords
As I mentioned earlier, using SSH keys is way better than using passwords. Here’s why:
- SSH keys are much harder to crack than passwords.
- You don’t have to worry about users forgetting or sharing passwords.
- SSH keys can be easily revoked if they’re compromised.
So, make sure you’re using SSH keys for all your IoT devices. It’s a simple step that can make a big difference in your security posture.
Regularly Updating Your Devices
Another important best practice is to keep your devices up to date. This includes updating firmware, software, and security patches. Outdated software is a common entry point for hackers, so don’t let it happen to you.
Common Challenges and Solutions
Of course, no guide would be complete without addressing some common challenges you might face when working with IoT SSH AWS. Let’s take a look at a few of them and how to solve them.
Managing Multiple Devices
As your IoT fleet grows, managing multiple devices can become a challenge. Here’s how to handle it:
- Use AWS IoT Device Management to organize and manage your devices.
- Automate tasks like firmware updates and configuration changes using AWS Lambda.
- Set up alerts and notifications for device issues using Amazon CloudWatch.
By leveraging AWS services, you can manage your devices more efficiently and reduce the risk of errors.
Dealing with Security Threats
Security threats are always a concern when working with IoT devices. Here’s how to protect yourself:
- Monitor your devices for suspicious activity using AWS IoT Device Defender.
- Use AWS WAF to block malicious traffic from reaching your devices.
- Regularly review and update your security policies to stay ahead of new threats.
By staying vigilant and proactive, you can minimize the risk of security breaches.
Conclusion
And there you have it, folks! Everything you need to know about securely accessing IoT devices via SSH on AWS. From setting up your devices to implementing best practices, we’ve covered it all. Remember, security is key when working with IoT devices, so don’t skimp on it.
Now, here’s your call to action: take what you’ve learned and start securing your IoT devices today. Whether you’re managing a smart home or an industrial plant, AWS has the tools you need to succeed. So what are you waiting for? Get out there and make it happen!
And don’t forget to share this article with your friends and colleagues. The more people who know about IoT SSH AWS, the better. Until next time, stay safe and keep innovating!
Table of Contents
- Understanding the Basics of IoT SSH AWS
- Why Use AWS for IoT SSH?
- Setting Up Your IoT Devices for SSH Access
- Creating a Secure Environment on AWS
- Using AWS IoT Core for Device Management
- Implementing Best Practices for IoT SSH AWS
- Common Challenges and Solutions
- Conclusion